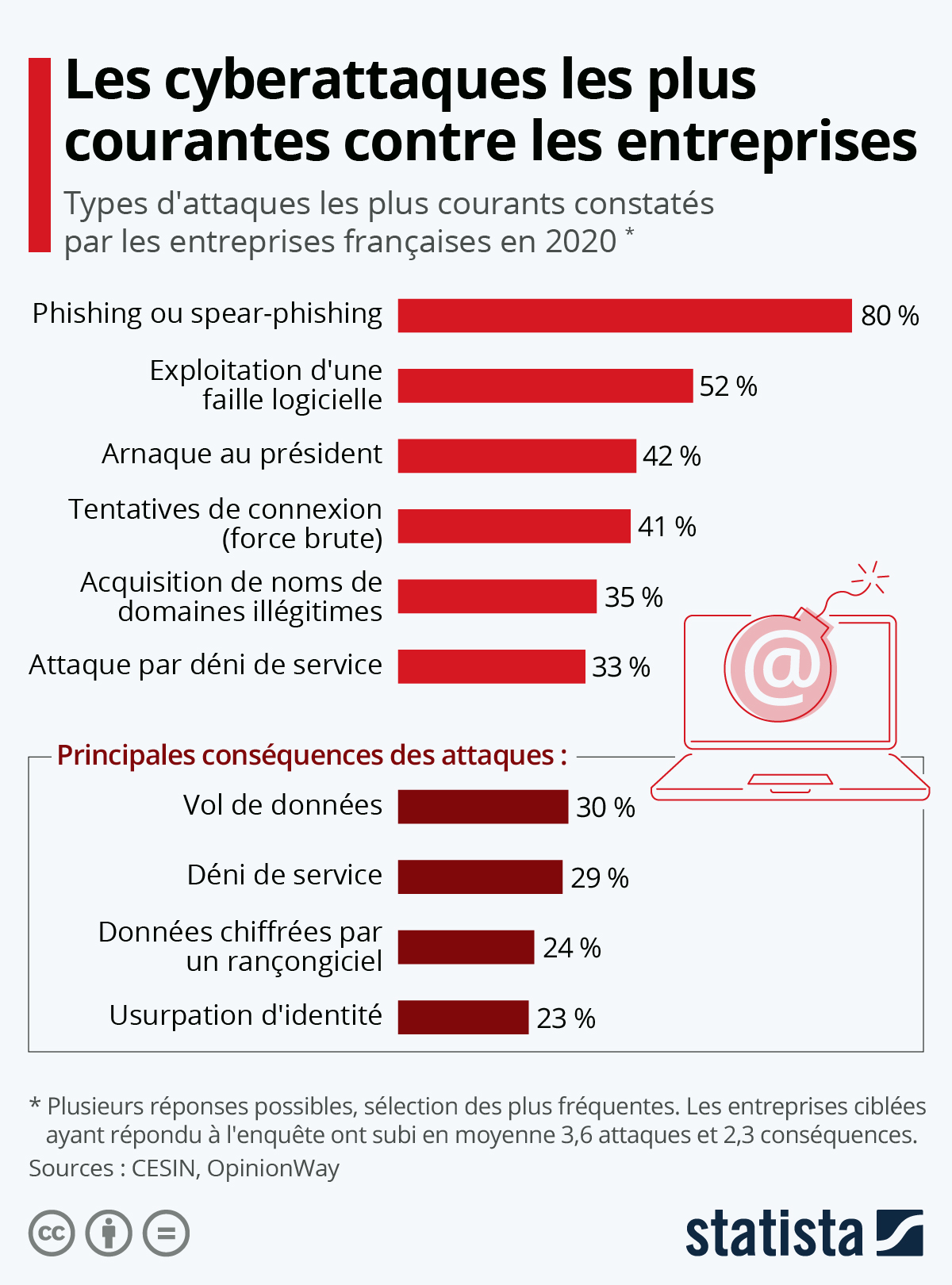
📨 Today the majority of attacks pass through emails. 📨
Effective solutions can be quickly put in place to counteract this problem:
✅ Through targeted training and internal company phishing campaigns
✅ Use of solutions such as Vade or MailInBlack which will, in most cases, prevent the transmission of spam.
But when the hacker is already in your company, it is difficult to know the actual impact without first having done a technical assessment that tests the security of your infrastructure.
🔎 An internal security audit is required 🔎
Several scenarios are possible:
💀 Malicious employee
💀 Malicious visitor
💀 Malicious or compromised provider
These scenarios can also be evaluated in the context of remote workers (telework and mobile workers).
This type of audit can also be used to test access:
📡 To Wi-Fi networks
🏬 To buildings and headquarters
The auditor verifies that the least privileges principle is applied at all different levels of the company:
📠 Clerk
📊 Accountant
🔧 Technician
💼 Service provider
Internal penetration testing can also be an opportunity to simulate a ransomware attack 💰.
This analysis allows customers to know their Information System weaknesses, define priorities to improve their security posture and reduce risks in case of cyber attack.
🛡️ DSecBypass supports you in IT security audits, with quality services and significant experience in this type of service. Do not hesitate to contact us for additional information 🤔 and / or a personalized quote 📝.